Securing DePINs Deployments and Digital Wallets with Comprehensive Risk Management and Control Measures
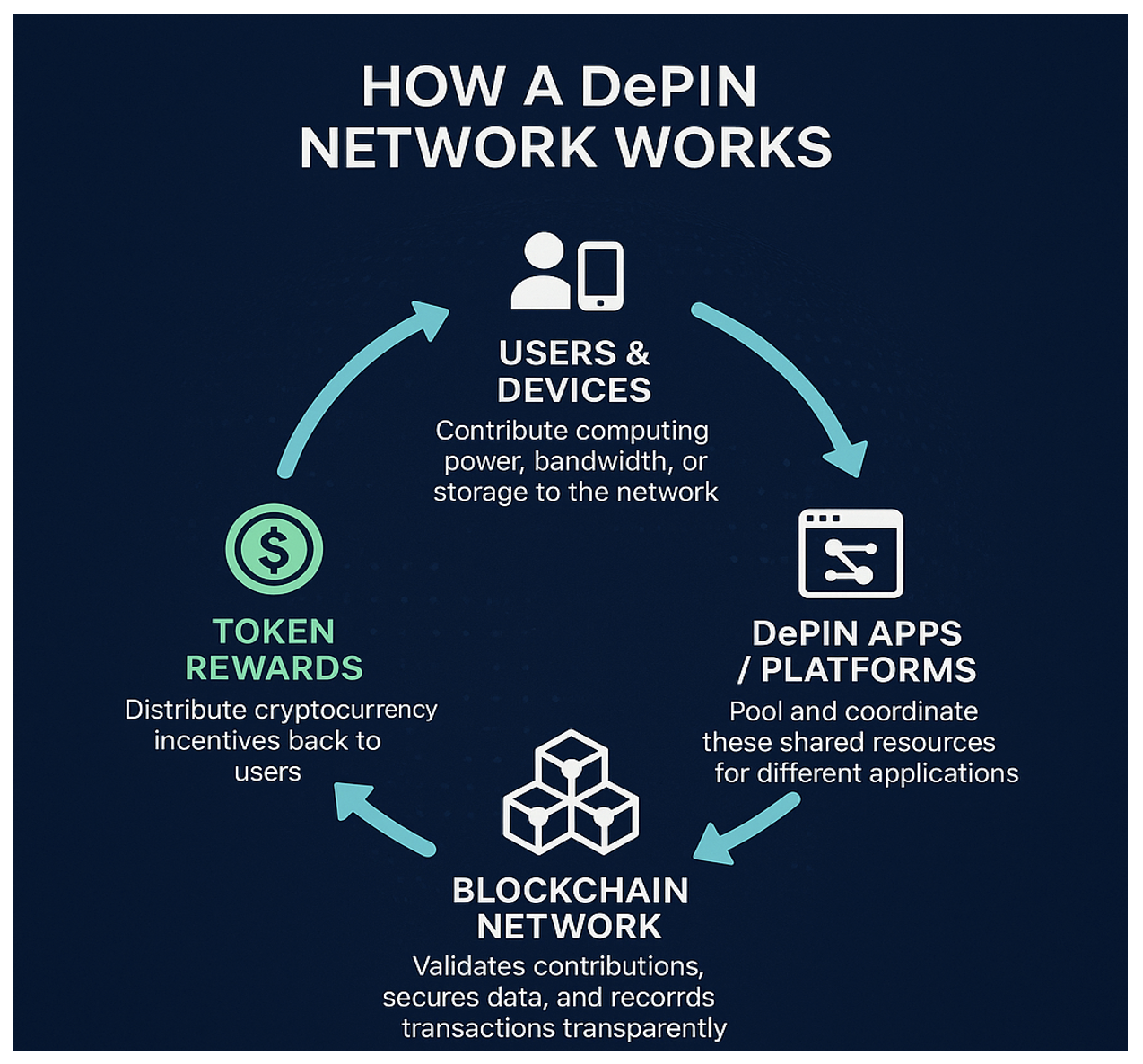
DePINs let users earn crypto by sharing device resources, but they also bring serious security risks. This article highlights the threats, statistics, and steps InfoSec professionals must take to protect decentralized infrastructure.
A new wave of applications pays you in cryptocurrency for sharing a bit of your device’s extra storage, bandwidth, or computing power. These are called DePINs (Decentralized Physical Infrastructure Networks). Simply put, you contribute resources and earn tokens in return. It sounds interesting, but it can also expose your phone and laptop to new risks. Hackers are constantly on the hunt for new vulnerabilities to steal data, drain crypto wallets, or exploit weaknesses in the network’s infrastructure. For professionals dealing with Information Security, the task is to support advanced technology adoption while enforcing basic security hygiene, strong controls, and continuous monitoring across users, devices, and vendors.
Key Statistics: DePIN Infrastructures Are a Goldmine for Hackers
Keeping DePIN’s infrastructure safe, the journey initiates with first protecting the people using them, the wallets they connect to, and the low-level systems lying underneath the abstraction layer. The numbers showcased below show how simple yet not so fancy robust security controls matter:
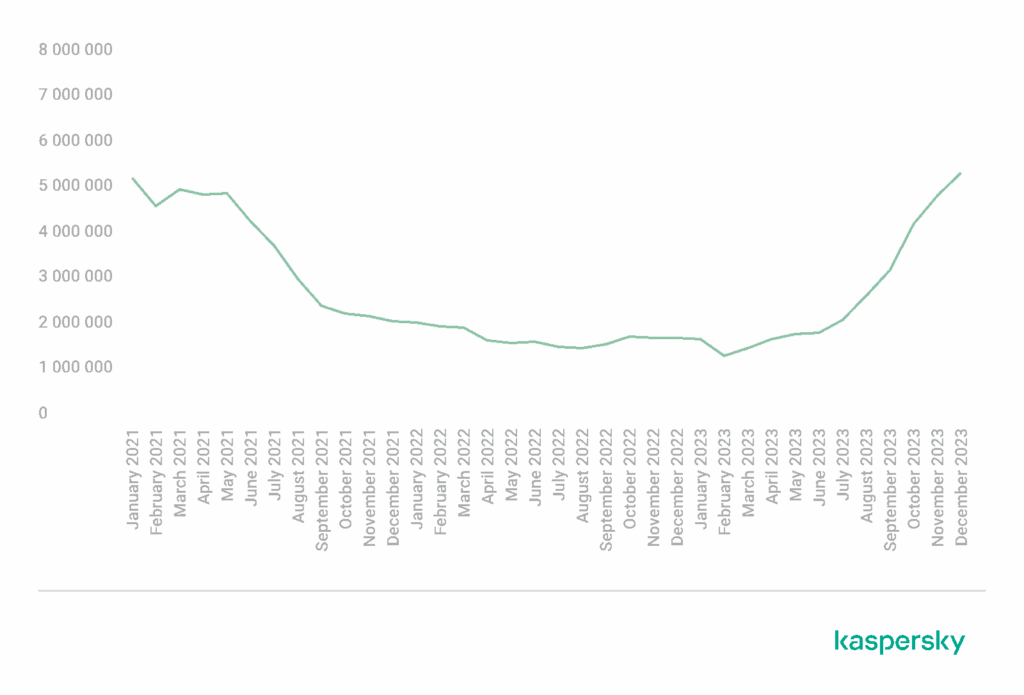
- As per the recent Kaspersky report, Attacks on mobile devices rose about 50 percent in 2023 to nearly 33.8 million. Since many DePIN users run apps on phones, basic security hygiene practices need to be leveraged.
- Hackers stole a record 3.8 billion USD in 2022, mainly from DeFi (Decentralized Finance) protocols. That surge shows decentralized systems being on the target radar.
- The global average cost for a data breach was documented as 4.45 million USD in 2023. A single compromise can be financially painful, making security investments essential.
- Victims reported over 6.5 billion USD in crypto investment fraud losses in the year 2024. Scam campaigns often orbit earn-crypto models, so users should verify projects and teams before connecting wallets.
DePINs Explained: Earning Crypto with Idle Resources
DePINs, or Decentralized Physical Infrastructure Networks, are blockchain-based ecosystems where people run small apps on their phones or computers and earn cryptocurrency in return, if put in words. You share your computing resources like processing power, bandwidth, or storage, and you get incentivized in return to contribute real-world infrastructure resources. This network model consists of nodes and devices where the computing resources are distributed across thousands of participating users, removing dependency on the centralized authority to govern exchanges. It is a simple idea with real upside. Still, it also means your device becomes part of a financial system, which can attract attackers if the underlying security configurations are weak.
Introducing Real-Life DePIN Application: UpRock
UpRock is a practical example of what DePINs models can do. It lets everyday users earn cryptocurrency by running light computing background tasks on their own devices. This approach turns idle resources into real value. It’s a simple win-win outcome: DePIN apps gain additional compute power, while users earn cryptocurrency rewards while doing what they already love: playing games, referring friends, receiving more innovative shopping options with fancy cashback offers, etc.
Of course, with any new technology, it’s essential to think about how it works. This births meaningful discussions around how best to handle user data, ensure payout systems are secure, and stay ahead of any potential vulnerabilities.
Exposing the Security Concerns Relating to DePINs
In the above paragraph, we learnt how DePIN’s technology is a real game-changer in the industry, but it comes with its fair share of risks we must be educated about. Some of the key risks associated with DePINs are as follows:
- Data Privacy Risks: Apps may collect sensitive device or location data. Combined, this information can reveal far more than expected and raise critical privacy issues and concerns, leading to non-compliance!
- Malware and Fake Apps: Some attackers tend to masquerade malware as authentic DePIN apps. A user might unknowingly install such an application, which can secretly harvest credentials or monitor activity.
- Crypto Theft and Fraud: Many DePIN model-based applications require wallet integration. If compromised, apps can steal seed phrases or redirect funds. Even users with comparatively low investments have reported losing tokens overnight!
- Network Vulnerabilities: Decentralized models spread responsibility. Without central oversight, patches and monitoring are inconsistent, leaving room for weak links.
From Risk to Resilience: How to Secure DePIN Deployments
Let’s not get demotivated by the security concerns we just learned; there are some real-life working tools or mitigation strategies that may help us tackle the situation. Please continue reading below:
- Install only trusted DePIN apps: Stick to official app stores or verified project sites only. Check the developer page, version history, reviews, and the last update date during installation, review permissions, and remove any app permissions that ask for more than they need.
- Keep devices updated and use multi-factor authentication: Turn on automatic updates for the operating system, browsers, and the DePIN app itself. Use multi-factor authentication on exchanges, wallets, and email accounts tied to crypto recovery functionality.
- Monitor wallets and set alerts for unusual activity: Use watch-only addresses or portfolio tools that notify you of incoming and outgoing transaction requests. Set daily transfer limits where possible for a lesser chance of huge monetary loss in case of.
- Use endpoint protection to detect abnormal behavior: Deploy endpoint detection and response that can spot suspicious processes, traffic spikes, or data exfiltration. Enable DNS filtering and application control to block known malicious domains and unapproved binaries.
Final Words
Looking at DePINs through a security lens, the upside is clear, and so are the risks. The numbers show how fast attackers are on the move. Take baby steps; first, start by focusing on simple mitigation strategies that work on a scale. Verify apps, harden endpoints, keep a close watch over monitor wallets, keep logs, enforce least privilege, and test your existing threat response plans. Stay current with compliance in every region you operate. With steady vigilance and disciplined operations, secure adoption is well within control and reach!
References
- Cryptocrime hit a record $14 billion in 2021, research shows. (2022, January 6). Reuters. https://www.reuters.com/markets/us/crypto-crime-hit-record-14-billion-2021-research-shows-2022-01-06/
- Kaspersky. (2024, February 26). Attacks on mobile devices significantly increased in 2023. /. https://www.kaspersky.com/about/press-releases/attacks-on-mobile-devices-significantly-increase-in-2023
- Kivva, A. (2024, February 26). The mobile malware threat landscape in 2023. Kaspersky. https://securelist.com/mobile-malware-report-2023/111964/
- Crypto hacks stole a record $3.8 billion in 2022, led by North Korea groups – report. (2023, February 1). Reuters. https://www.reuters.com/technology/crypto-hacks-stole-record-38-billion-2022-led-by-north-korea-groups-report-2023-02-01/
- IBM Report: Half of Breached Organizations Unwilling to Increase Security Spend Despite Soaring Breach Costs. (n.d.). IBM Newsroom. Retrieved August 18, 2025, from https://newsroom.ibm.com/2023-07-24-IBM-Report-Half-of-Breached-Organizations-Unwilling-to-Increase-Security-Spend-Despite-Soaring-Breach-Costs
- FBI Releases Annual Internet Crime Report. (2025, April 23). Federal Bureau of Investigation. https://www.fbi.gov/news/press-releases/fbi-releases-annual-internet-crime-report
- UpRock. (n.d.). UpRock., from https://uprock.com

Comments are closed.